Introduction
This post is to help users be able to assign administrative roles to Enterprise Applications/Service Principals so that they can perform duties that would otherwise require a user with elevated permissions to accomplish. This is convenient when a user wishes to use a service principal in order to reset a password, or to perform some activity that requires admin privileges programmatically without an interactive sign in (using client credentials grant type flow).
In this post we will go over installing MSOnline (MSOL) PowerShell module, finding the Object ID for your Enterprise Application, and then giving the Enterprise Application an administrative role.
Note: We will be using MSOnline powershell cmdlets, these are a bit outdated. So as of 8-29-2018 they have not been deprecated yet, however please be sure to check the status of MSOL library. The history for the AAD libraries can be found here: https://social.technet.microsoft.com/wiki/contents/articles/28552.microsoft-azure-active-directory-powershell-module-version-release-history.aspx
We will be using Version 1.1.166.0 (PowerShell V1 General Availability)
You can also utilize AAD powershell V2.0. We will be going over this as well.
Prerequisite
In order to add an Application role to a Service Principal, you will need to have the proper permissions to assign roles to objects. Per the documentation here : https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/directory-assign-admin-roles#details-about-the-global-administrator-role
You will need to be a Global Administrator in order to set the roles to the Enterprise Application. Please be sure to get the global admin to perform to set the Enterprise Application to have the administrative privilege.
Getting Started with MSOL
In order to add the application role to a service principal we will have to utilize the older MSOL powershell Cmdlets.
In order to install MSOL, open up PowerShell and type in :
Install-Module -Name MSOnline
You can find the library in the PowerShell gallery here : https://www.powershellgallery.com/packages/MSOnline/1.1.183.17
After you have installed MSOL, you will need to login to your Azure Active Directory using MSOL. In order to do this use the command :
Connect-MsolService
There should now be a popup asking you to login to Azure. Be sure to use a global admin account, otherwise you won’t be able to follow the next step to give an enterprise application an administrative role.
Getting Started with AAD PowerShell V2.0
This document goes over install AAD Powershell V2.0:
https://docs.microsoft.com/en-us/powershell/azure/active-directory/install-adv2?view=azureadps-2.0
Similar to installing MSOL.
You will utilize the commands :
Install-Module AzureAD
Connect-AzureAD
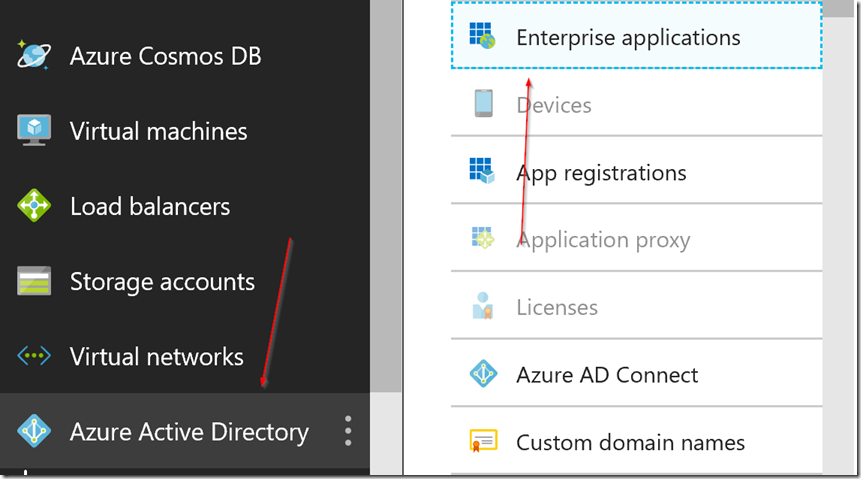
Getting the ObjectID of the Enterprise Application
Now we need to get the Object ID from the Enterprise Application. There are two ways you can do this, you can get the Object ID from the powershell CMDlet, or you can go to the Azure Portal and get the object ID from the Enterprise Application under the properties blade.
Using MSOL Powershell
Here we will take a look at a short script you can utilize in order to get the object ID of the Enterprise Application assuming you know the Application Registration Application ID.
$tenantID = “<ID for Tenant>”
$appID = “<Application ID>”
$msSP = Get-MsolServicePrincipal -AppPrincipalId $appID -TenantID $tenantID
$objectId = $msSP.ObjectId
Using AAD V2.0 PowerShell
You can also utilize AAD powershell v2.0 using the command :
$mysp = Get-AzureADServicePrincipal -searchstring <your enterprise application name>
$mysp.ObjectId
Now we have the service principal stored in the variable $mysp. We will use it later to associate a role to the enterprise application.
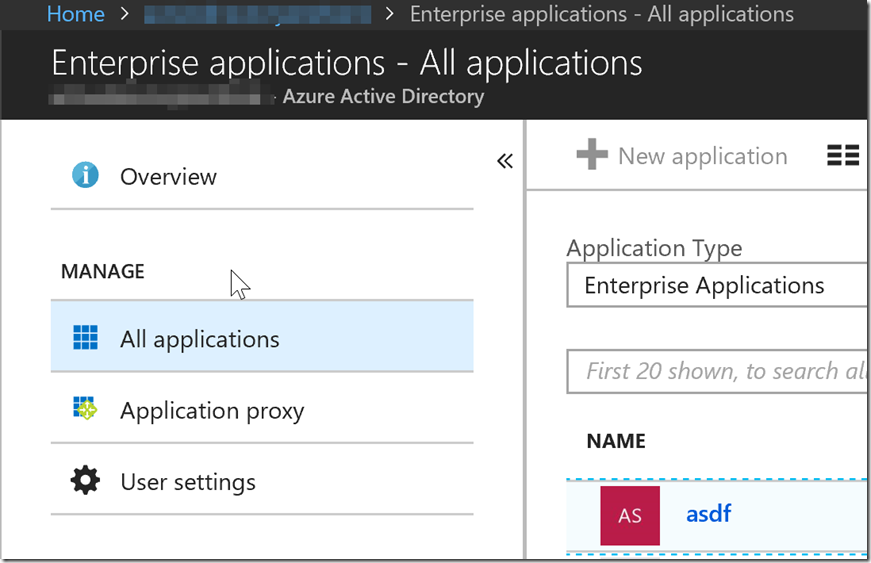
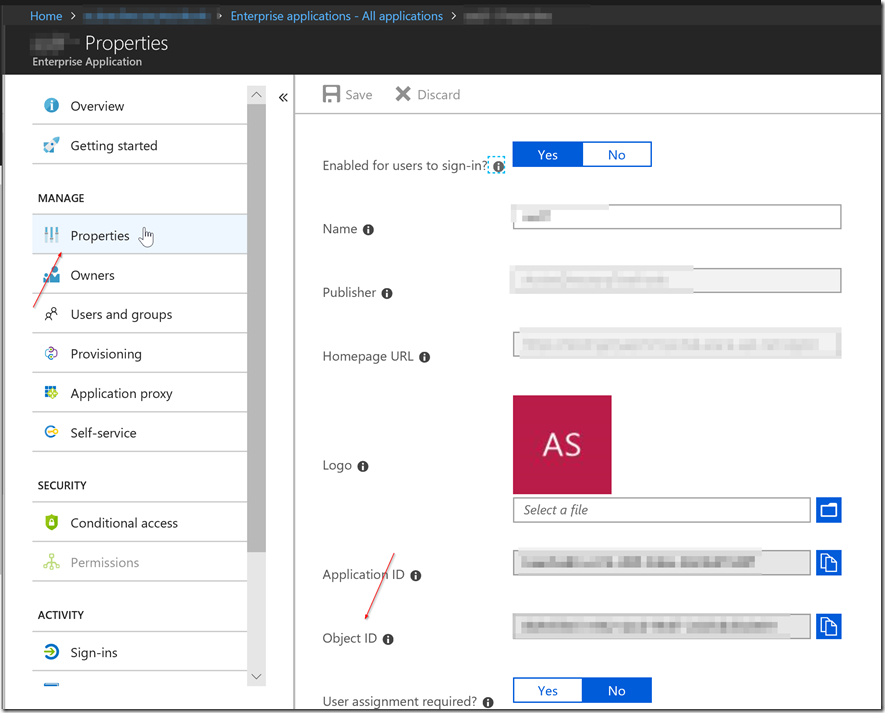
Using the Azure Portal
To get the ObjectID through the Azure Portal, you will need to go to portal.azure.com. From there go to Azure Active Directory on the left side bar. Then to Enterprise Applications > All Applications > (Your Enterprise Application to set to an Admin Role) > Properties > Object ID.
Assigning an Administrative Role for an Enterprise Application
First please make sure you have the Administrative Role Name on hand as you will need it in order to add the Admin Role to the Enterprise Application. You can find all the roles here: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/directory-assign-admin-roles
In this Example we will be using Helpdesk Administrator
Using MSOL to Add a Role Member
All we have to do is run the MSOL PowerShell cmdlet Add-MsolRoleMember.
This PowerShell Cmdlet is described in detail here : https://docs.microsoft.com/en-us/powershell/module/msonline/add-msolrolemember?view=azureadps-1.0.
For our intents and purposes, we can use this one liner in order to set the Enterprise Application to have the Admin Role :
Add-MsolRoleMember -RoleName “Helpdesk Administrator” -RoleMemberType ServicePrincipal -RoleMemberObjectId $objectId
Replacing ObjectID with the enterprise application’s ObjectID if you don’t have $objectID saved.
We have successfully added the admin role to the enterprise application.
Note: This may require some time to take effect.
Using Azure AAD Powershell V2 to Add a Role Member
When using AAD PowerShell v2, you will need to get the object ID of the AAD role, you can utilize this command below to get the information.
$myAADRole = Get-AzureADDirectoryRole | Where-Object {$_.displayName -eq ‘Helpdesk Administrator’}
$myAADRole.ObjectId
Now that we have the object IDs for the AAD role, we will need to get both object IDs to add the role to the enterprise application. We can use the command below :
Add-AzureADDirectoryRoleMember -ObjectId $myAADRole.ObjectId -RefObjectId $mysp.ObjectId
Replacing the variables with the object IDs if you don’t have the variables saved.
We have successfully added the admin role to the enterprise application.
Note: This may require some time to take effect.
Conclusion
In this article we have gone over downloading MSOL and AAD V2.0, connecting with MSOL and V2.0, getting the object id for the enterprise application, getting the Application Role in MSOL and AAD V2.0, and giving the enterprise application the admin role using both AAD V2.0 and MSOL. you should now have an enterprise application that can do the actions that typically require a user with the admin privileges described in the role. If you have anymore issues feel free to open a support ticket or comment below and either one of our support engineers or I will try to assist you in this endeavor.
This seems really out of date, is there a more current version? Also what are the PowerShell commands to modify the other Enterprise Application properties like Provisioning – Automatic, and SSO?
This article is currently up to date as of 10-12.
The AAD V2.0 powershell Commands are the most up to date commands. Utilizing AAD V2.0 commands are shown in this article as well.
If you would like to take a look at the reference for Service principal commands for AAD related powershell cmdlets, the reference can be found here : https://docs.microsoft.com/en-us/powershell/module/azuread/?view=azureadps-2.0#service_principals
AAD V2.0 doesn’t have any support for provisioning and SSO as the AAD v2.0 powershell library utilizes the Microsoft Graph API.
MSOL won’t support it because MSOL libraries aren’t being updated for newer features.
There are no specific mappings from the AAD Enterprise Application Provisioning/SSO blades to Powershell cmdlets.
Awesome post.